In the age of hyper-connectivity, data has become the lifeblood of our world. From our online identities to our financial transactions, everything seems to exist in the digital realm. This convenience, however, comes with a critical responsibility: data security. Protecting our valuable information from malicious actors and unforeseen breaches is a constant challenge, demanding an ever-evolving approach.
This article dives deep into the intricate world of data security, offering insights into its core principles, the latest threats, and innovative solutions. Whether you’re a tech enthusiast or simply concerned about your online privacy, consider this your comprehensive guide to navigating the data-driven landscape securely.
The Pillars of Data Security:
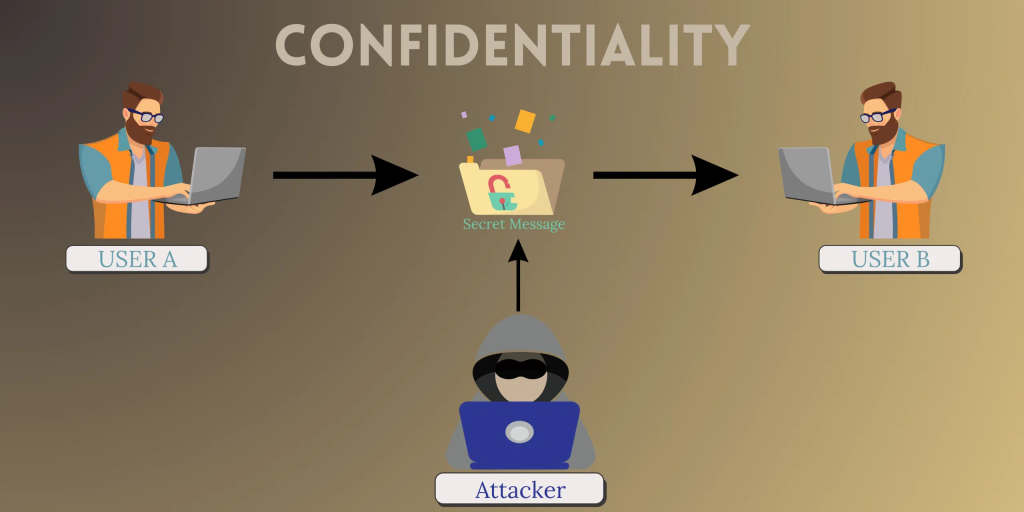
- Confidentiality: Ensuring only authorized individuals access sensitive information. Think encryption, access controls, and identity management.
- Integrity: Protecting data from unauthorized modification or manipulation. Data checksums, digital signatures, and tamper-evident logs play crucial roles here.
- Availability: Guaranteeing authorized users have timely access to data when needed. Redundancy, disaster recovery plans, and reliable infrastructure are key.
Emerging Threats on the Horizon:
- Deepfakes: AI-powered video and audio manipulation techniques posing severe threats to personal reputations and national security.
- Supply chain attacks: Exploiting vulnerabilities in software and firmware to compromise entire ecosystems, highlighting the need for secure development practices.
- Quantum computing: While still in its infancy, quantum computing could potentially render current encryption methods obsolete, demanding cryptographic advancements.
Navigating the Security Landscape:
- Strong passwords and multi-factor authentication: The first line of defense against unauthorized access. Use unique, complex passwords and consider biometric authentication methods.
- Beware of phishing scams: Never click on suspicious links or download attachments from unknown sources. Verify sender identities and double-check URLs before interacting.
- Keep software updated: Patching vulnerabilities regularly is crucial. Enable automatic updates for operating systems and essential applications.
- Backup your data: Protect against accidents and intentional attacks by regularly backing up your data to offline or secure cloud storage.
Latest News in Data Security:
- Cybersecurity industry booming: Cybersecurity spending is expected to reach $418 billion globally by 2025, reflecting the growing awareness of data security threats.
- Focus on privacy regulations: Data privacy laws like GDPR and CCPA are reshaping how organizations collect and use personal data, putting user control at the forefront.
- Zero-trust security gaining traction: Traditional perimeter-based security models are giving way to zero-trust architectures, requiring continuous verification for every access attempt.
Beyond the Buzzwords:
Data security is not just a technical issue; it’s a human one. Fostering security awareness within organizations and educating individuals about online safety practices are critical to building a robust defense against cyber threats. Additionally, collaboration between cybersecurity experts, policymakers, and technology developers is essential to develop innovative solutions and stay ahead of evolving threats.
Your Role in Data Security:
As individuals, we all play a role in protecting our data. By following basic security practices, staying informed about the latest threats, and demanding accountability from data handlers, we can contribute to a safer digital future. Remember, security is a shared responsibility; let’s work together to secure our digital lives and build a more trustworthy online world.
TechBrushHub Resources:
This article is just the beginning of your data security journey. TechBrushHub is committed to providing you with up-to-date information and practical advice on all things tech. Explore our website for in-depth articles, insightful tutorials, and expert reviews on data security tools and technologies. Stay informed, stay protected, and join us in building a secure and thriving digital ecosystem.





Leave a Reply